Azure Private Endpoint DNS integration : one policy to rule them all !
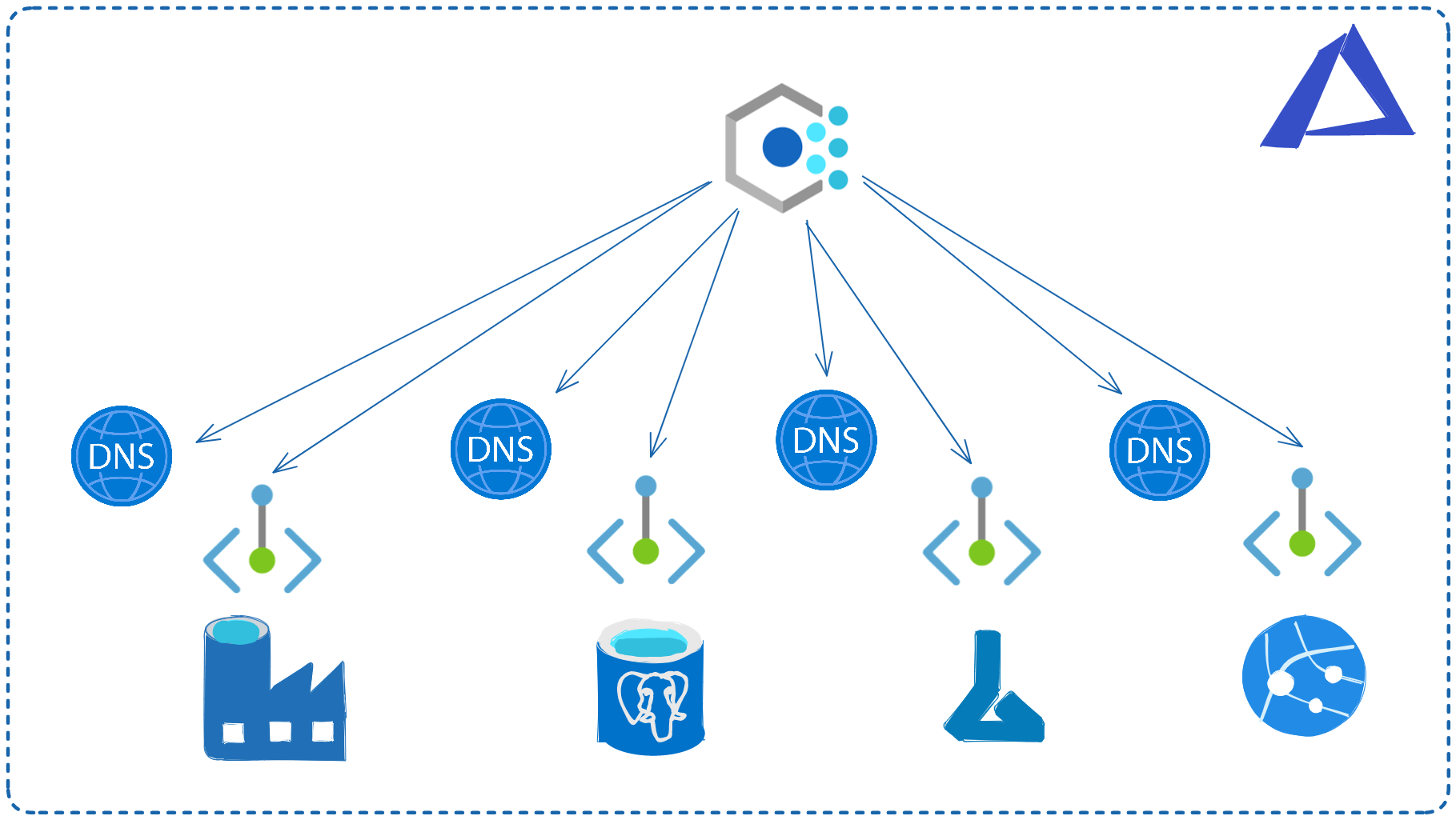
How to resolve Private Endpoint with a private IP ?
The challenge with Private Endpoint is clearly the DNS integration and configuration. It's important to correctly configure the DNS to resolve the endpoint name with the private IP address.
Microsoft Azure services already have a DNS configuration for a public endpoint. This configuration must be overridden to connect using private endpoint.
Let's take this example:
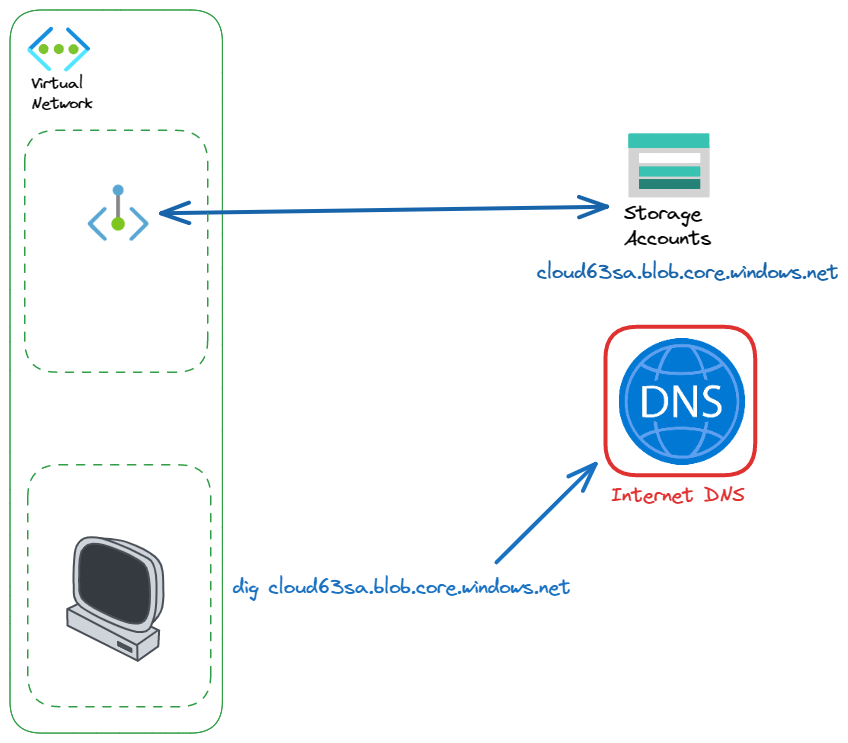
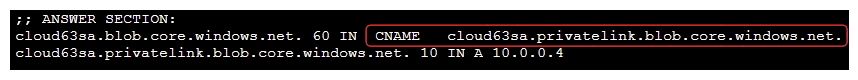
As soon as you create a private endpoint, Azure will automatically create a CNAME pointing to a specific private link zone. Using standard DNS, you must see something like this :
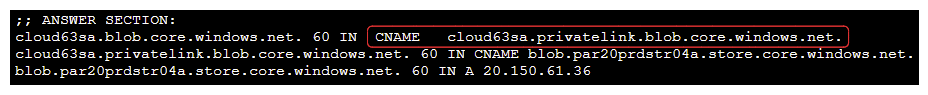
Thanks to DNS recursivity, you must be able to finally resolve Storage Account FQDN with a public IP.
But we want to be able to resolve Storage Account FQDN with the private endpoint IP. It can be done directly on the hosts file but it cannot be the solution at scale.
Azure Private DNS zone to the rescue
With Azure Private DNS zone, you can create your own DNS zone and manage the DNS records.
To be able to use this zone, there is 2 conditions : use Azure DNS Virtual Server IP address (168.63.129.16) as DNS server and create a VNet Link between the VNet and the Private DNS Zone.
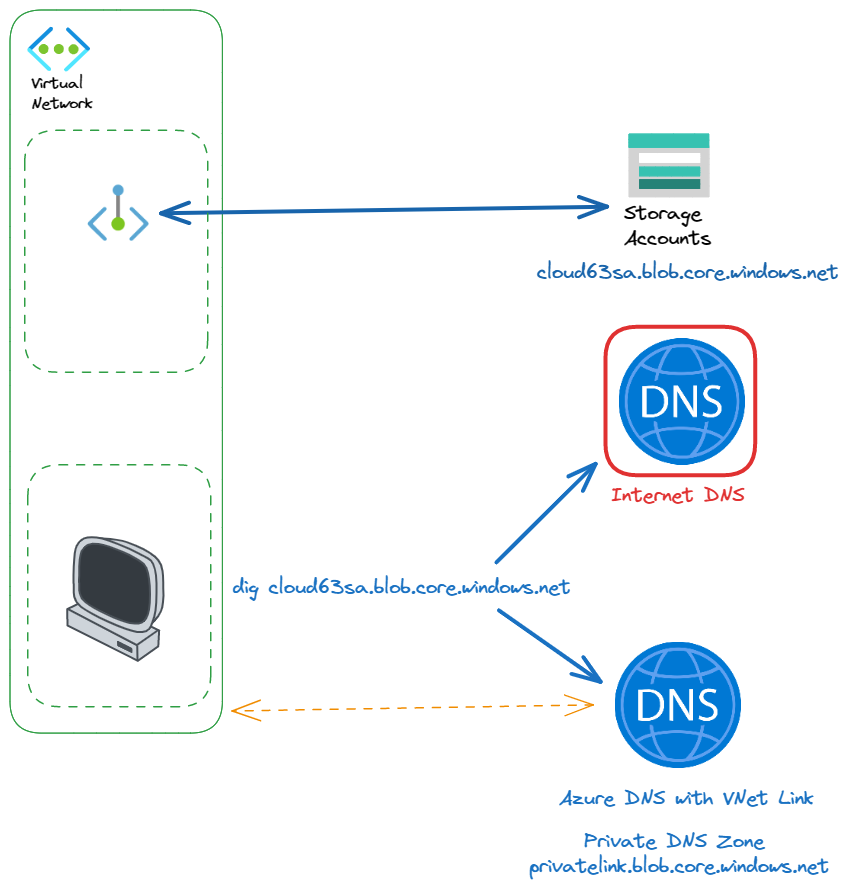
The network interface associated with the private endpoint contains the information to configure DNS. The network interface information includes FQDN and private IP addresses for the private link resource. If you create the Private Endpoint using Azure Portal, you can diretcly deploy this configuration on the corresponding DNS zone.
Once the configuration is done, you must be able to resolve FQDN with private IP:
Private Endpoint DNS integration at scale
You cannot have multiple VNet link for the same zone to the same VNet. If you have a central DNS infrastructure, you want to manage centrally all the Private DNS zones.
First solution can be to keep control on all the private endpoint deployment and provisioned the DNS entry on the correct zone. But if you want to give autonomy to the user, you will have to find another solution.
Azure recommanded solution is to use Azure Policy : Private Link and DNS integration at scale - Cloud Adoption Framework | Microsoft Learn
There is many built-in Azure Policy to manage several type of Private Endpoint and even an Initiative with all the policies : Configure Azure PaaS services to use private DNS zones (azadvertizer.net)
But each time you want to integrate a new type of private endpoint you will have to find the correct policy or wait to have it created (some are still missing today).
One policy to rule them all !
Based on this template, I have created a new Azure Policy being able to address all type of private endpoint.
This policy needs 3 parameters :
- privateEndpointPrivateLinkServiceId : Private Endpoint Link Service Id
- privateEndpointGroupId : Private Endpoint Group Id
- privateDnsZoneIds: Array of Private DNS Zone Id
privateEndpointPrivateLinkServiceId & privateEndpointGroupId are used to identify the type of private endpoint. privateDnsZoneIds is a list of DNS private zone to register private endpoint.
The mapping is directly available on Microsoft documentation.
This policy can be deploy manualy using Azure CLI :
az policy definition create --name 'AzurePaaSPrivateDNSZone' \
--rules "`jq '.[].policyRule' deploy-policy.json`" \
--params "`jq '.[].parameters' deploy-policy.json`"
You have to create in advance the Private DNS Zone corresponding to private endpoint you want to manage with the policy and then you can create one assignment.
For example fo Storage account blob :
az policy assignment create --name 'private-dns-storageAccounts-blob' \
--policy 'AzurePaaSPrivateDNSZone' \
--mi-system-assigned \
--location westeurope \
--params '{"privateDnsZoneIds": {"value": [ "/subscriptions/00000000-0000-0000-0000-000000000000/resourceGroups/private-dns-zones-rg/providers/Microsoft.Network/privateDnsZones/privatelink.blob.core.windows.net"]},\
"privateEndpointGroupId": {"value": "blob"},\
"privateEndpointPrivateLinkServiceId": {"value": "Microsoft.Storage/storageAccounts"}}'
I worked on a Terraform script to help the deployment for all the zones and all the policies.
You just need to use the scripts available in this repo. You can review and edit the mapping in file : private-zones.json and customize options in file : variables.tf Once everything is ready, you just have to start terraform deployment :
terraform init
terraform plan
terraform apply
After several minutes, everything must be deployed:

You will have one dedicated Resource Group for Private DNS Zone:

If you check on Policy Assignments you must have all the assignments done for all the kinds of private endpoint:

You can try to deploy any private endpoint and automatically after few seconds the entry must be created on the corresponding private DNS zone.
As the policy is working with Private DNS Zone Config, if you delete the private endpoint, the DNS record will be automatically deleted.
Conclusion
Private Endpoint is really a great feature but DNS integration can be a real nightmare. With this policy and the Terraform scripts, you can setup in one time and in few minutes all the infrastructure to manage Private Endpoint DNS integration at scale.
Don't hesitate to contact me if you have any question or remark.