Azure Firewall implementation in hub and spoke architecture
Quick presentation
Azure Firewall is a Firewall in PaaS in other term it's a managed, cloud-based network security appliance. It's a fully stateful firewall as a service with built-in high availability and scalability.
Since few months now, Azure Firewall has 2 tiers : Standard and Premium.
Azure Firewall Standard provide basic firewall functionality : L4 filtering, DNS proxy, Application filtering (http / https) but if you need more advance security features like IDPS (Intrusion Detection and Prevention Systems) or TLS Inspeciton you will have to choose Premium tier.
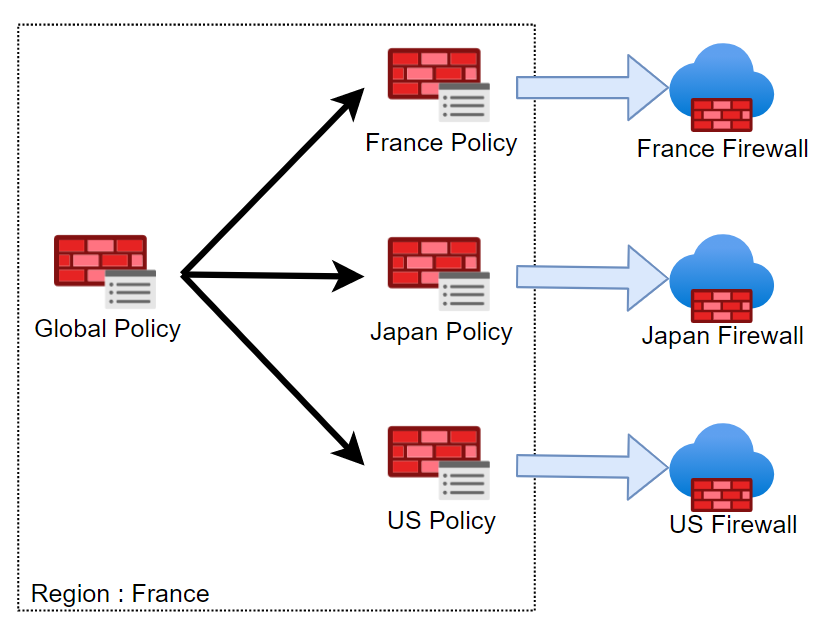
Azure Firewall uses Firewall Policy, a global resource that can be used to centrally manage your firewalls using Azure Firewall Manager. A Firewall Policy can be see as a firewall configuration with filtering rule sets & security feature configuration. A firewall policy associated with a single firewall has no charge. A firewall policy (child) can inherit from an other firewall policy (parent) of the same tier (standard or premium). Parent policy must be in the same region as child policy but firewall policy can be associated with firewalls across regions.
Implementation
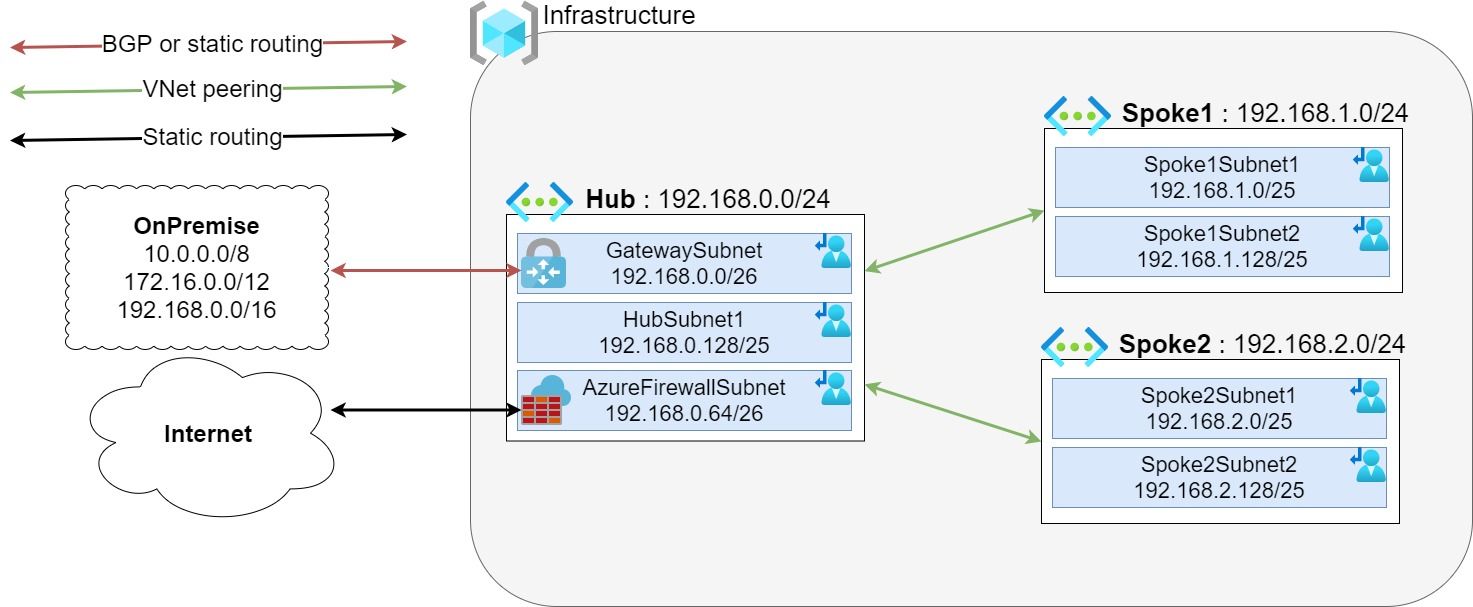
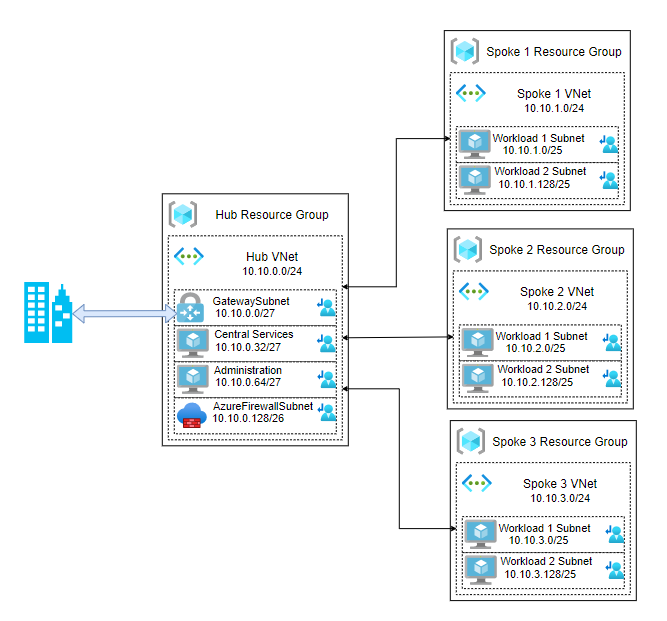
As an example, let's take the following standard hub and spoke architecture:
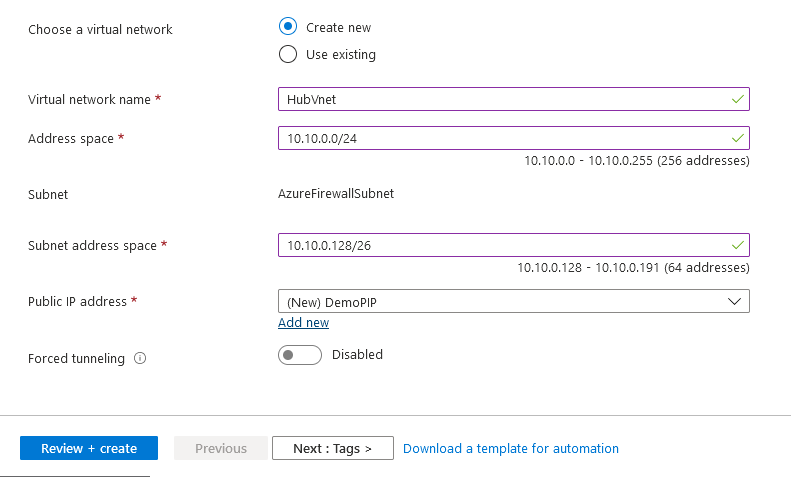
Azure Firewall is a central network component so it's logical to deploy it in the hub part. Like Azure Virtual Network Gateway, Azure Firewall will require a dedicated subnet with a specific naming convention : AzureFirewallSubnet. This subnet will required a /26 to have enough space for automatic scaling.
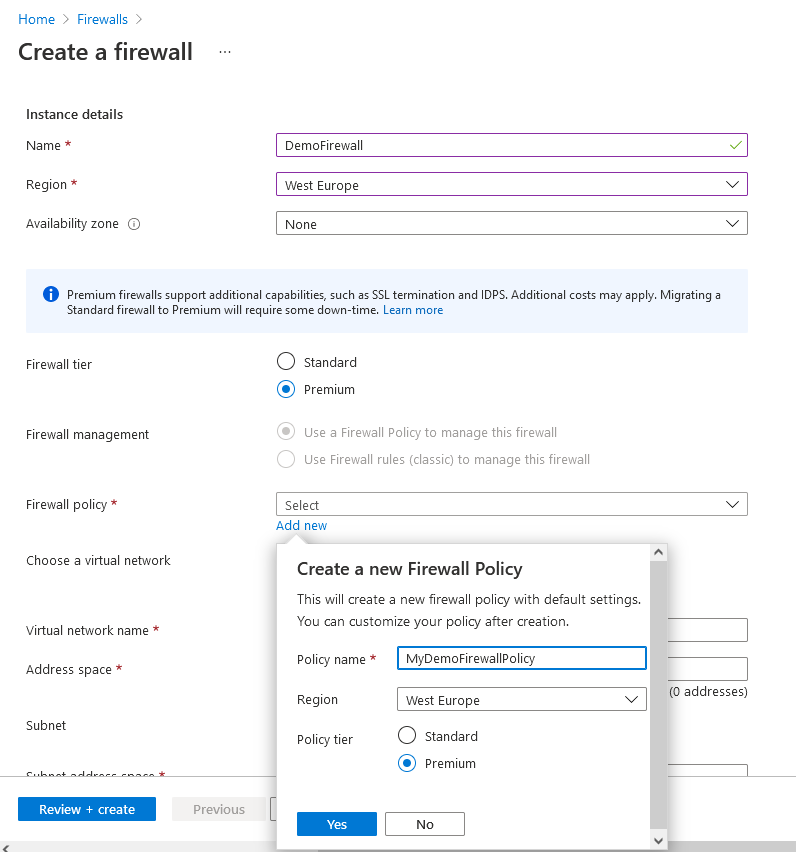
Provisioning using Azure Portal:
Provisioning using Terraform:
resource "azurerm_subnet" "subnet" {
name = "AzureFirewallSubnet"
resource_group_name = "DemoRG"
virtual_network_name = "Hubvnet"
address_prefixes = "10.10.0.128/26"
}
resource "azurerm_public_ip" "public_ip" {
name = "Demo-PIP"
location = "westeurope"
resource_group_name = "DemoRG"
allocation_method = "Static"
sku = "Standard"
}
resource "azurerm_firewall" "firewall" {
name = "DemoFirewall"
location = "westeurope"
resource_group_name = "DemoRG"
sku_tier = "premium"
firewall_policy_id = "MyDemoFirewallPolicy"
ip_configuration {
name = "DemoFirewall-ipconfiguration"
subnet_id = azurerm_subnet.subnet.id
public_ip_address_id = azurerm_public_ip.public_ip.id
}
}
Azure Firewall provisioning can take until 15 minutes to be up and running.
Route tables
Create the Azure Firewall is really easy but the complex part is to route the traffic through this device. In a standard hub and spoke architecture, the routing is managed by Azure and routes are automatically created with VNet peering and connection on Virtual Network Gateway.
With Azure Firewall in the architecture, route table are mandatory to override Azure’s default routing. A route table contains routes and is associated to one or more subjects.
At least 3 route tables are required to managed correctly the routing :
- Gateway Route Table
- Propagate gateway routes: Yes
- Overwrite hub and spoke VNet routes through Azure Firewall - Hub Route Table
- Propagate gateway routes: No
- Overwrite hub and spoke VNet routes through Azure Firewall
- Inject OnPrem routes through Azure Firewall - Spoke Route Table
- Propagate gateway routes: No
- Overwrite hub VNet routes through Azure Firewall
- Overwrite Default through Azure Firewall
All this deployment can be done manually but I recommend you to automate this. Even if it can be manageable for small deployment (or PoC) for big infrastructure it can be a source of issue. With automation, you will be able to implement the switch from a standard hub and spoke to hub and spoke protected by Azure Firewall in only few minutes with only few seconds a downtime.
To help you on this deployment, I have written a Terraform module available on GitHub : https://github.com/vmisson/terraform-azure-firewall
This module will help to manage easily your routing and facilitate your migration to Azure Firewall.
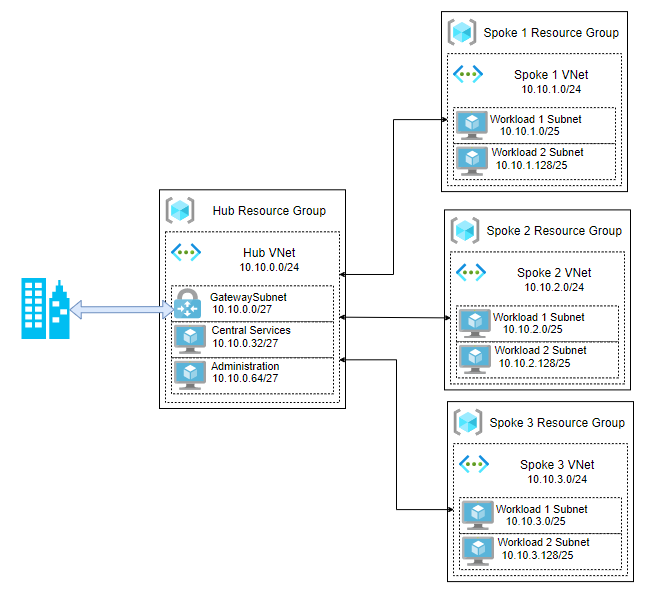
After provisioning your hub and spoke architecture will look like:
After the implementation, on the next article will go deeper on the configuration of Azure Firewall.
Links
- Azure Hub&Spoke archi : https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/ready/azure-best-practices/hub-spoke-network-topology
- Azure Firewall documentation : https://docs.microsoft.com/en-us/azure/firewall/overview
- Azure Firewall pricing : https://azure.microsoft.com/fr-fr/pricing/details/azure-firewall/
- Terraform module Azure Firewall Hub & Spoke deployment : https://github.com/vmisson/terraform-azure-firewall