Azure Gateway Load Balancer
"Gateway Load Balancer is a SKU of the Azure Load Balancer portfolio catered for high performance and high availability scenarios with third-party Network Virtual Appliances (NVAs). With the capabilities of Gateway Load Balancer, you can easily deploy, scale, and manage NVAs. Chaining a Gateway Load Balancer to your public endpoint only requires one selection." This is the official description from Microsoft documentation. We will see in this article how to deploy Azure Gateway Load Balancer and the problem it can solve.
How to deploy Azure Gateway Load Balancer
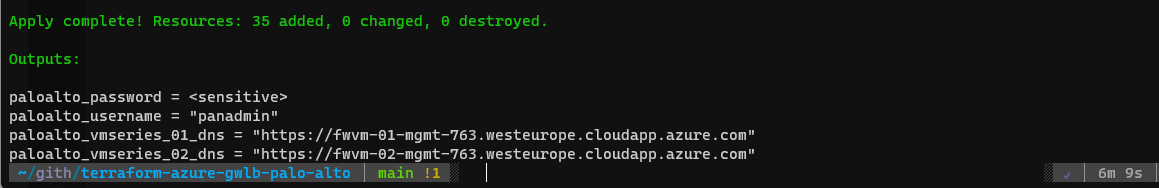
To simplify the deployment of Gateway Load Balancer, you can use the following Terraform scripts : vmisson/terraform-azure-gwlb-palo-alto (github.com)
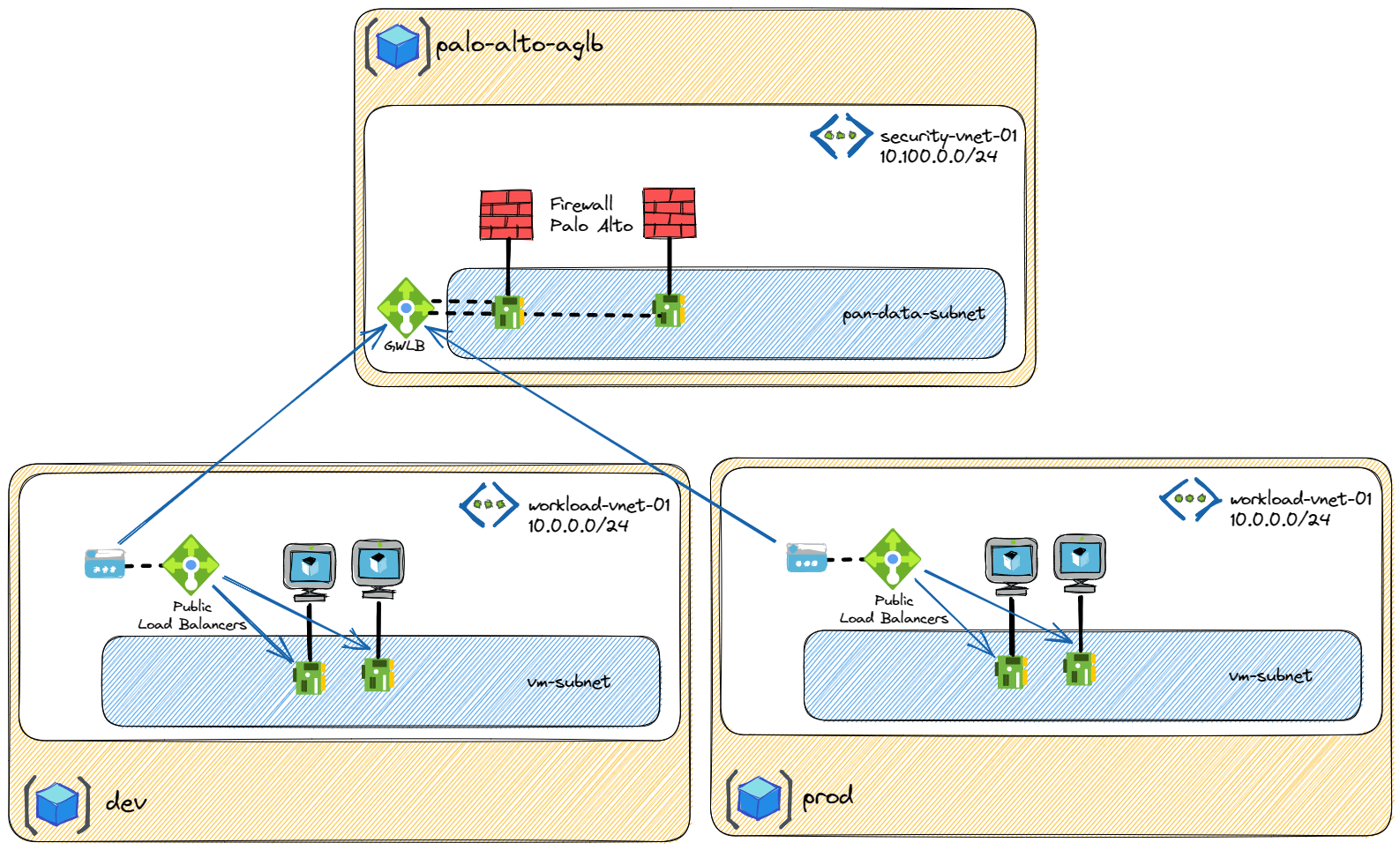
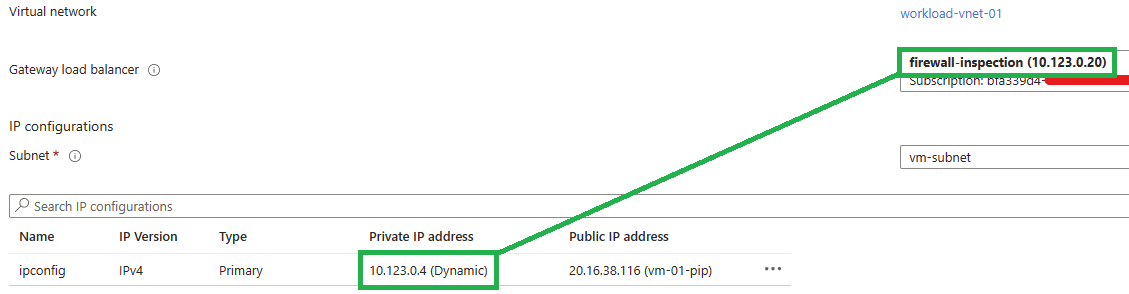
You just have to update the allow_inbound_mgmt_ips variable in the variables.tf file with you public IP and run Terraform. After few minutes, you must have the following infrastructure ready to use:
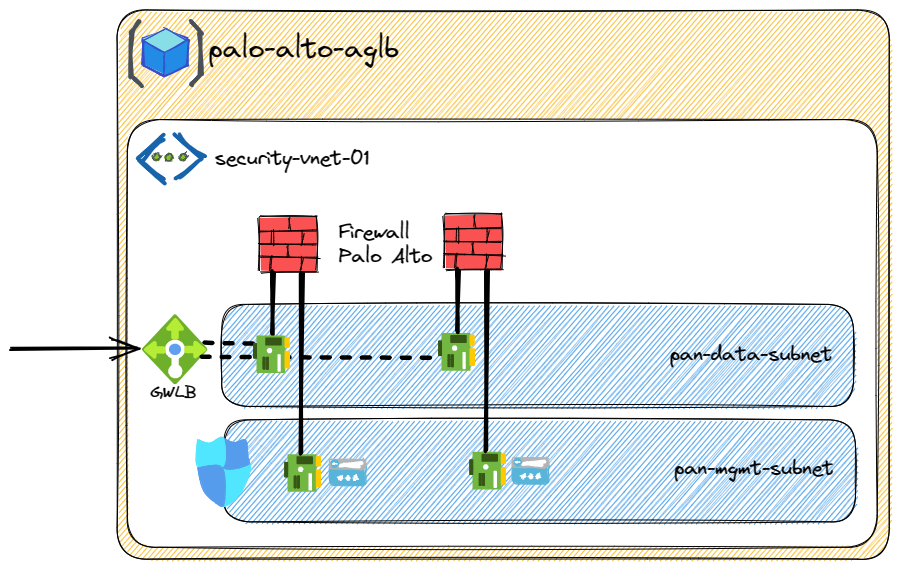
Azure Gateway Load Balancer was design to be a standalone cluster with multiple NVA behind it. If you want to inspect and secure traffic, you don't have to route the traffic as we do for "normal" load balancer but you have to use chaining.
A Standard Public Load balancer or a Standard IP configuration of a virtual machine can be chained to a Gateway Load Balancer. Once chained to a Standard Public Load Balancer frontend or Standard IP configuration on a virtual machine, no extra configuration is needed to ensure traffic to, and from the application endpoint is sent to the Gateway Load Balancer.
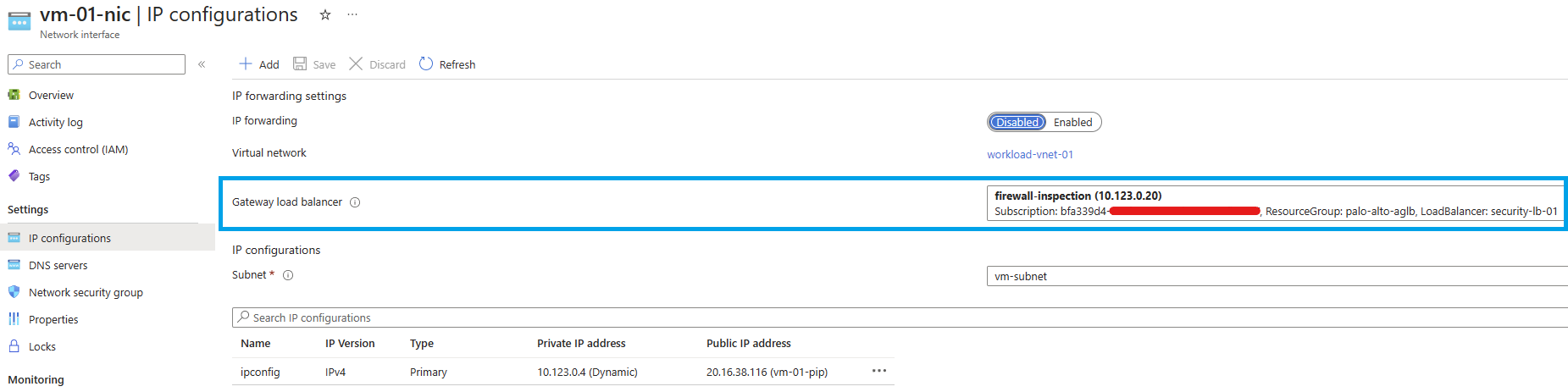
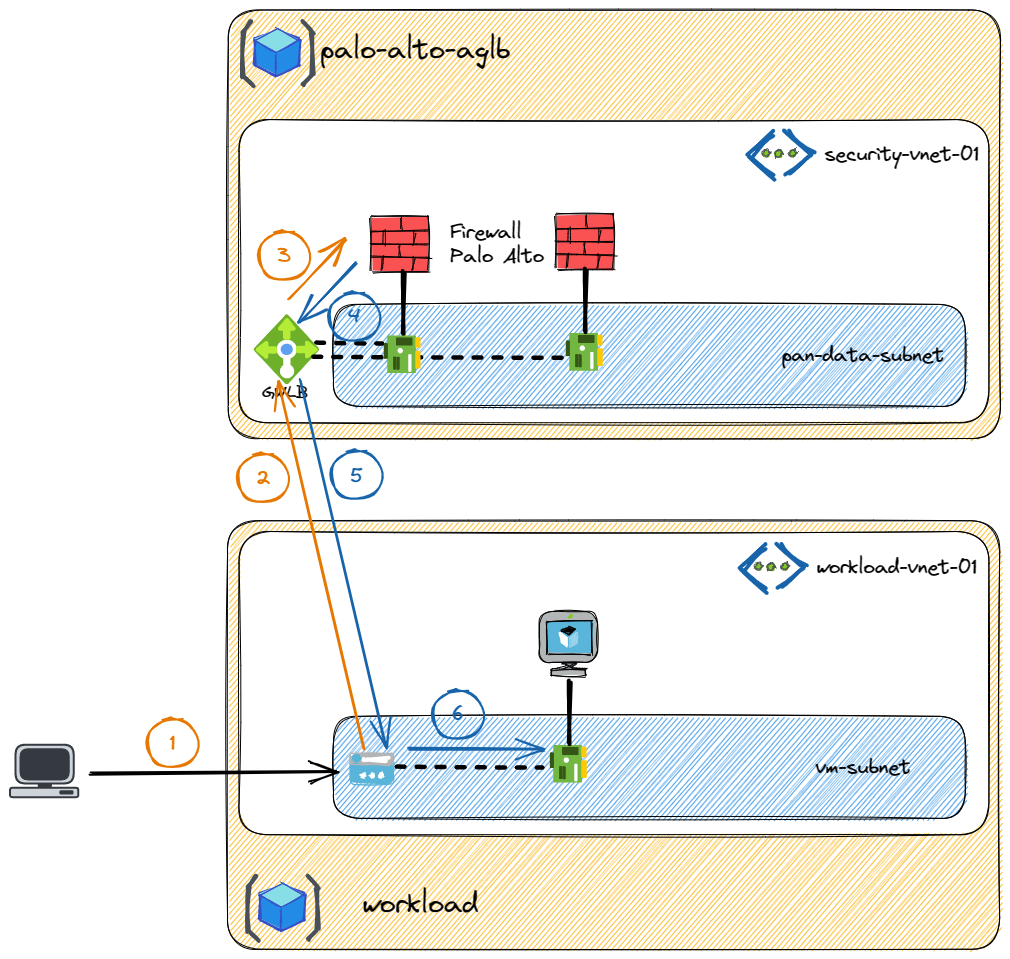
In this example the client wants to access a service running on a VM with a public IP attached to it (1). The public IP is chained to the Gateway Load Balancer so the traffic is forwarded to it (2). Using VXLAN, the packet is encapsulated and transferred to one of the firewall (3). If the traffic is allowed by firewall, it will go back to the Gateway Load Balancer (4) then to the public IP (5) before being translate to VM private IP (6).
The firewall will see only the public traffic as the chaining is always before the IP translation (for public IP and for public Load Balancer).
Thanks to VXLAN, this solution is working even if there is IP overlapping between your VNets.
Problems solved by Azure Gateway Load Balancer
Manage active-active firewall cluster easily
Configure an active-active firewall in Azure can be sometimes complicated. Azure Gateway Load Balancer has been design to manage this use case. You have have only one Load Balancer to manage inbound and outbound traffic so you don't have to manage flow symetry.
Add security to VM directly exposed on internet
If you have to expose directly a VM on Internet with a public IP, Azure Gateway Load Balancer can help you to add interesting security feature. Depending of the NVA you have behind your Gateway Load Balancer, you can insert transparently : filtering, IDP/IPS, traffic mirroring or captures...
With public Load Balancer, even if you expose only some services, it can be interesting to have this security layer on top.
Manage IP overlapping
IP address exhaustion or IP address overlapping are common problem. Using Azure Gateway Load Balancer, you can deploy independent application environment with exactly the same IP range but you are still able to provide security in a central firewall cluster.
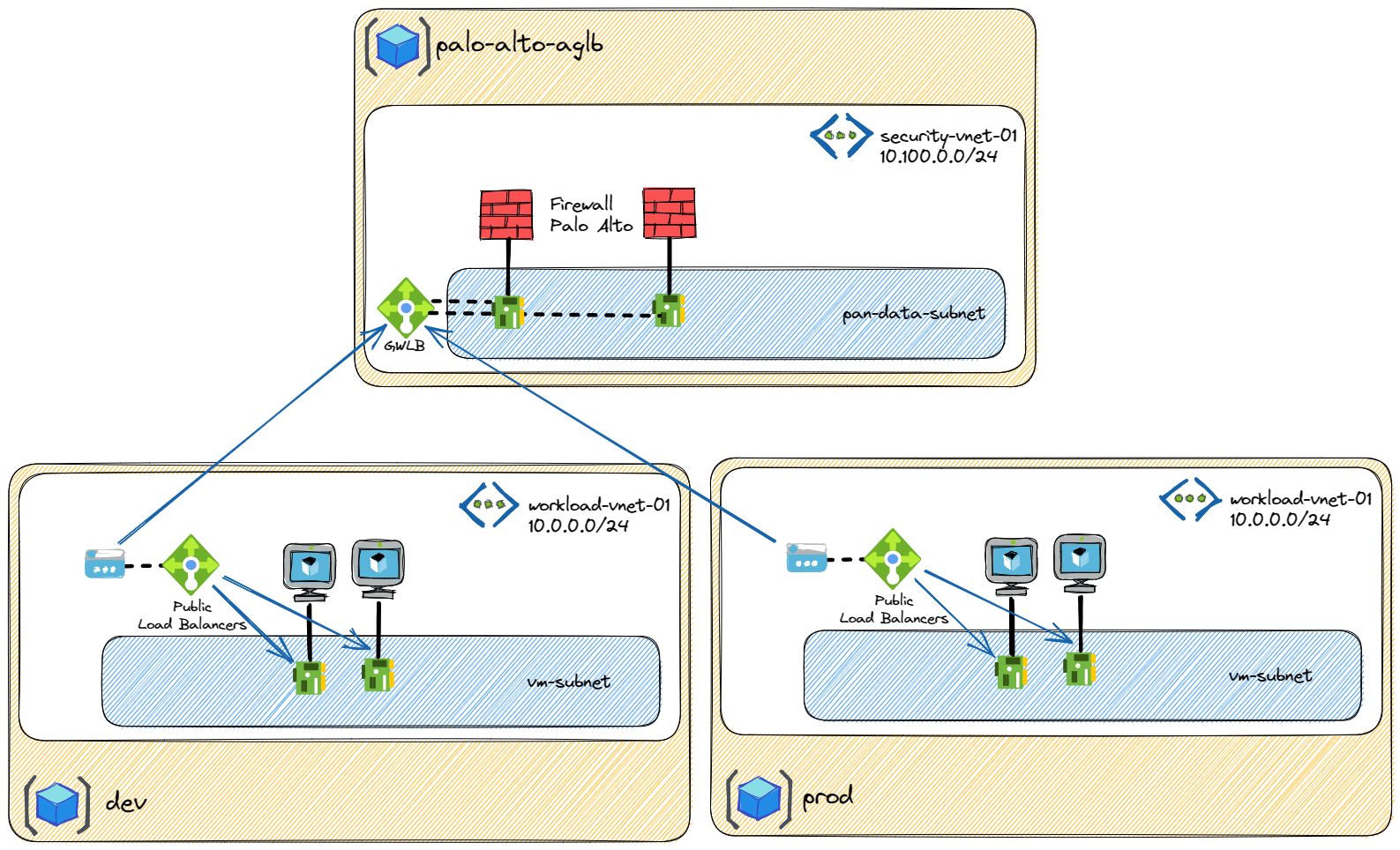
Another possible scenario would be the need to control independent environments (lab for example) without having to manage the IP addresses of the users.
This solution can be extended to multiple AKS cluster using kubnet. One Azure Gateway Load Balancer in front of multiple AKS can limit the cost and the management of having multiple firewall clusters to manage.
Conclusion
It was a first look on Azure Gateway Load balancer. Using my Terraform scripts, you can easily deploy your own firewall cluster and start to use Gateway Load Balancer. As explained, this Load Balancer was design to bring transparently additional security layer without changing the routing.
Overall, Azure Gateway Load Balancer is a powerful tool for managing network traffic and improving the security of your application.
Don't hesitate to contact me if you have any question or remark and don't forget to launch terraform destroy at the end of your tests ;-)